Last updated by: buvan008, Last updated on: 08/09/2024
Malware Outbreak Incident Red Team Usecase
Malware Outbreak Incident Red Team Usecase
Effective Date: 6 May 2024. Last Edited: 4 May 2024. Author: Liya Thomas Document Reference: MORTU-1. Expiry Date: 6 May 2025. Version: 1.0.
1. Introduction:
Within the landscape of cybersecurity, the Data Theft Playbook emerges as a beacon of guidance, offering Red Teams a meticulously crafted roadmap to simulate and evaluate an organization's preparedness against data breaches and unauthorized intrusions. By orchestrating a series of simulated attacks, Red Teams embark on a mission to dissect the organization's security posture, scrutinize incident response protocols, and extract invaluable insights aimed at bolstering overall resilience against data theft incidents. This comprehensive guide serves as a compass, navigating Red Teams through the complex terrain of cybersecurity challenges, with the ultimate goal of fortifying the organization's defenses against the relentless tide of cyber threats.
2. Worms
2.1 Objective:
Stop the worm from spreading further, remove it from infected systems, and patch security vulnerabilities to prevent future infections.
2.2 Steps:
- Isolate infected systems to prevent further spread: Isolation of infected systems is crucial to prevent the worm from spreading to other devices on the network. This can be achieved by disconnecting the infected systems from the network or by creating VLANs to segregate them from the rest of the network traffic.
- Identify the entry point and security vulnerabilities exploited by the worm: Determining how the worm entered the system and the vulnerabilities it exploited is essential for effectively containing and eradicating it. This may involve analyzing system logs, examining network traffic, and conducting vulnerability assessments using tools such as Nessus or OpenVAS.
- Use network monitoring tools to analyze unusual traffic patterns: Network monitoring tools like Wireshark or Snort can help in detecting and analyzing unusual traffic patterns associated with the worm's activity. By monitoring network traffic in real-time, administrators can identify suspicious behavior and take appropriate action to mitigate the threat.
- Employ antivirus or antimalware software to detect and remove worm infections: Antivirus or antimalware software such as Norton, McAfee, or Malwarebytes can be deployed to detect and remove worm infections from infected systems. It's important to ensure that antivirus definitions are up-to-date to effectively identify and quarantine malicious files associated with the worm.
- Apply security patches and updates to vulnerable systems: Patch management is crucial for addressing security vulnerabilities exploited by the worm. Administrators should promptly apply security patches and updates to vulnerable systems to prevent future infections. Patch management tools such as Microsoft SCCM or WSUS can automate the patching process and ensure that systems are adequately protected against known vulnerabilities.
2.3 Tools and Techniques:
- Network traffic analysis tools like Wireshark or Snort:Wireshark is a widely used network protocol analyzer that allows administrators to capture and interactively browse the traffic running on a computer network. Snort is an open-source network intrusion detection system (NIDS) and network intrusion prevention system (NIPS) that can monitor network traffic for suspicious activity and take action to block or alert on potential threats.
- Antivirus software such as Norton, McAfee, or Malwarebytes: Antivirus software plays a crucial role in detecting and removing malware infections, including worms. Norton, McAfee, and Malwarebytes are popular antivirus solutions that offer real-time protection against a wide range of threats, including worms, viruses, and Trojans.
- Patch management tools to apply security updates promptly: Patch management tools automate the process of applying security patches and updates to vulnerable systems, ensuring that they are protected against known vulnerabilities. Microsoft SCCM (System Center Configuration Manager) and WSUS (Windows Server Update Services) are commonly used patch management solutions for Windows environments, while tools like Red Hat Satellite are available for managing patches in Linux environments.
3. Trojans
3.1 Objective:
Identify and remove Trojan malware, close backdoors, and strengthen security measures to prevent future intrusions.
3.2 Steps:
- Identify suspicious processes or applications running on infected systems: Identifying Trojan malware often involves monitoring system processes and applications for any suspicious behavior. Task Manager or similar tools can be used to identify processes consuming high CPU or memory resources, which may indicate the presence of a Trojan. Additionally, security information and event management (SIEM) solutions can help in correlating system events to pinpoint potential malicious activity.
- Investigate changes made to files and system settings by the Trojan: Trojans typically make changes to files, registry settings, or system configurations to maintain persistence and facilitate unauthorized access. File integrity monitoring (FIM) tools can be employed to detect any unauthorized modifications to critical system files or configurations. By analyzing these changes, administrators can identify the extent of the infection and take appropriate remediation measures.
- Use intrusion detection systems to monitor and block unauthorized access attempts: Intrusion detection systems (IDS) play a crucial role in detecting and preventing unauthorized access attempts by Trojans or other malicious actors. IDS solutions like Snort or Suricata can analyze network traffic in real-time to identify suspicious patterns or anomalies indicative of a Trojan infection. By configuring appropriate rules and alerts, administrators can block malicious traffic and prevent further infiltration.
- Remove Trojan payloads and associated files: Once the Trojan malware is identified, it's essential to remove its payloads and associated files from infected systems. Antivirus or antimalware software can be used to scan and quarantine malicious files, ensuring that the Trojan is effectively neutralized. Additionally, manual inspection and removal of suspicious files and registry entries may be necessary to eradicate the infection completely.
- Educate users about safe browsing and downloading practices: User awareness and education are critical components of any effective cybersecurity strategy. Training programs should educate users about the risks associated with downloading files from unknown sources, clicking on suspicious links, or opening email attachments from unfamiliar senders. By promoting safe browsing habits and encouraging vigilance, organizations can mitigate the risk of Trojan infections resulting from social engineering attacks.
3.3 Tools and Techniques:
- Intrusion Detection Systems (IDS) like Snort or Suricata:IDS solutions monitor network traffic for signs of malicious activity, including unauthorized access attempts and suspicious behavior indicative of Trojan infections. Snort and Suricata are open-source IDS platforms that use signature-based detection, anomaly detection, and protocol analysis to identify and block potential threats in real-time.
- Endpoint detection and response (EDR) tools such as CrowdStrike or Carbon Black: EDR solutions provide advanced threat detection and response capabilities at the endpoint level, allowing administrators to detect and remediate Trojan infections across their network. CrowdStrike and Carbon Black are leading EDR platforms that offer continuous monitoring, threat hunting, and automated response features to protect against sophisticated threats like Trojans.
- User training and awareness programs to prevent social engineering attacks: User training programs should educate employees about the tactics used by cybercriminals to distribute Trojan malware, such as phishing emails, malicious websites, or fake software downloads. By raising awareness about these threats and providing guidance on how to recognize and avoid them, organizations can empower users to play an active role in preventing Trojan infections and other cybersecurity incidents.
4. Ransomware
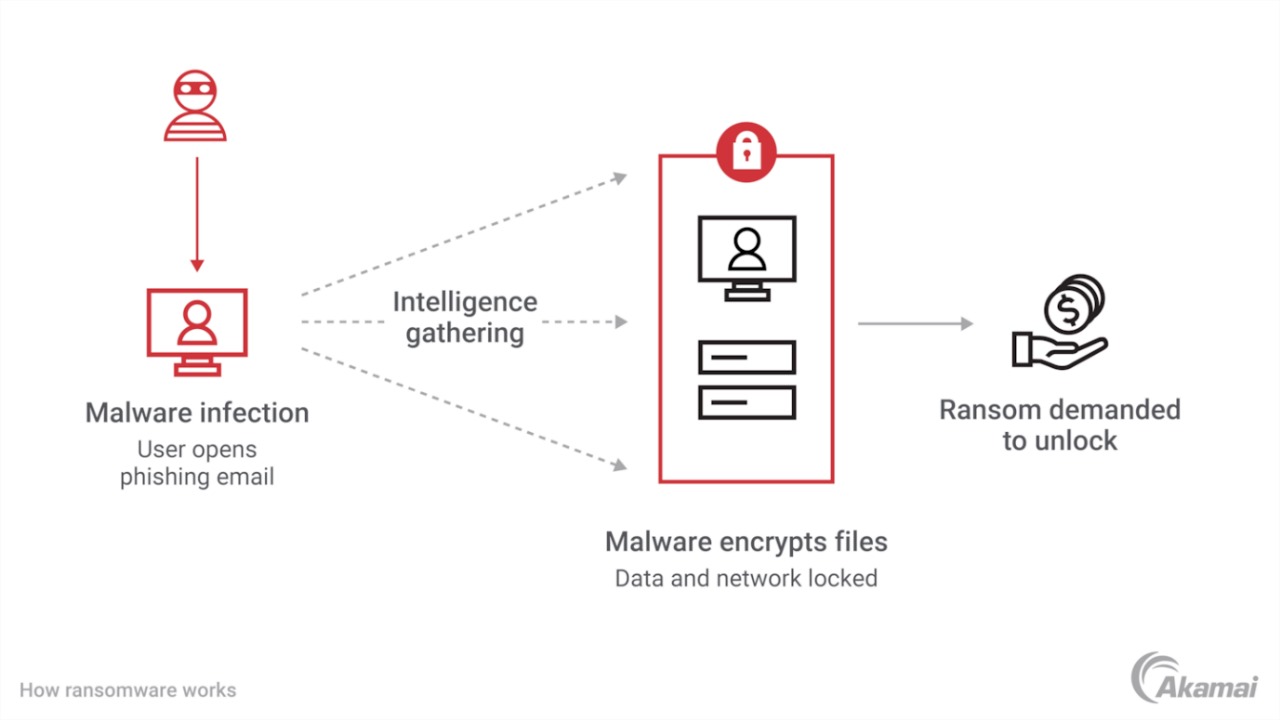
4.1 Objective:
Decrypt files if possible, remove ransomware, restore affected systems from backups, and implement security measures to prevent future attacks.
4.2 Steps:
- Disconnect infected systems from the network to prevent further encryption: It's crucial to isolate infected systems from the network to prevent the ransomware from spreading to other devices or encrypting additional files. This can help contain the impact of the attack and prevent further damage to data and systems.
- Identify the type of ransomware and check for available decryption tools: Identifying the specific type of ransomware infecting the systems is essential for determining if there are any decryption tools available. Websites like NoMoreRansom provide resources and decryption tools for various ransomware strains. Researching the ransomware variant can help in finding decryption keys or tools that may assist in recovering encrypted files without paying the ransom.
- Restore affected files from backups if available: If backups are available and unaffected by the ransomware attack, restoring files from backup is the most effective way to recover encrypted data. Backup and recovery solutions such as Veeam or Acronis can automate the restoration process, ensuring that critical data is quickly recovered without paying the ransom.
- Remove ransomware from infected systems: After disconnecting the infected systems and restoring files from backups, it's essential to remove the ransomware from the affected systems to prevent further damage. Antivirus or antimalware software can be used to scan and remove ransomware infections from infected devices, ensuring that the systems are clean and secure.
- Enhance security with robust backup solutions, endpoint protection, and user training: To prevent future ransomware attacks, it's essential to implement robust security measures across the organization. This includes investing in comprehensive backup solutions that regularly backup critical data to secure locations, endpoint security solutions with ransomware protection features that can detect and block ransomware attacks in real-time, and user training programs to educate employees about the risks of ransomware and best practices for avoiding infection.
4.3 Tools and Techniques:
- Ransomware decryption tools like NoMoreRansom: NoMoreRansom is a collaborative initiative between law enforcement agencies and cybersecurity organizations that provides resources and decryption tools for various ransomware strains. These tools can help victims recover encrypted files without paying the ransom, mitigating the financial impact of the attack.
- Backup and recovery solutions such as Veeam or Acronis: Backup and recovery solutions are essential for protecting against ransomware attacks by ensuring that critical data is regularly backed up and can be quickly restored in the event of an attack. Veeam and Acronis are leading providers of backup solutions that offer features such as automated backups, data deduplication, and encryption to safeguard against data loss and ransomware attacks.
- Endpoint security solutions with ransomware protection features: Endpoint security solutions play a critical role in protecting devices from ransomware attacks by detecting and blocking malicious activity in real-time. These solutions often include features such as behavior monitoring, file reputation analysis, and ransomware-specific detection algorithms to identify and mitigate ransomware threats before they can cause damage.
5. Botnet
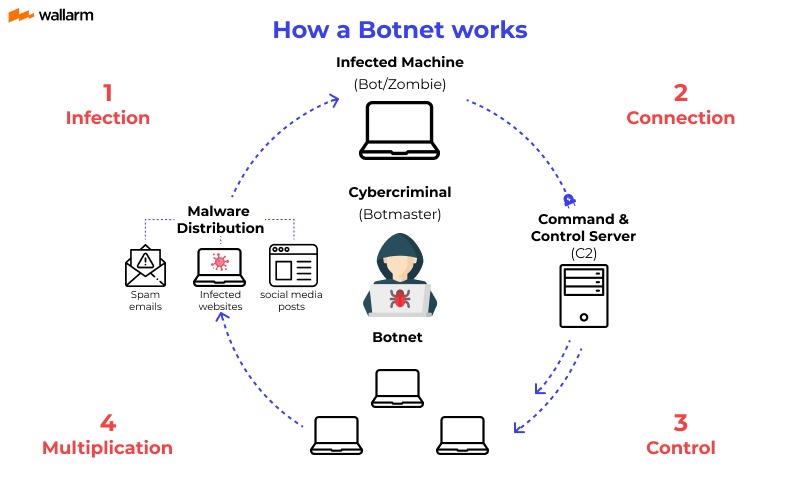
5.1 Objective:
Disrupt communication between compromised devices and command-and-control servers, remove botnet malware, and strengthen network defenses.
5.2 Steps:
- Identify compromised devices communicating with command-and-control servers: Detecting compromised devices communicating with botnet command-and-control (C&C) servers is crucial for mitigating botnet activity. Network monitoring tools and intrusion detection systems (IDS) can help identify suspicious network traffic patterns indicative of botnet communications.
- Block communication channels between infected devices and the botnet's infrastructure: Once compromised devices are identified, it's essential to block communication channels between these devices and the botnet's infrastructure. Network security appliances like firewalls and intrusion prevention systems (IPS) can be configured to block traffic to and from known botnet C&C servers, effectively disrupting the botnet's operations.
- Use antivirus or antimalware software to remove botnet malware: Removing botnet malware from infected devices is crucial for restoring their integrity and preventing further participation in the botnet. Antivirus or antimalware software can scan and remove botnet-related files and processes from compromised devices, ensuring that they are clean and secure.
- Implement network segmentation and access controls to contain the botnet: Implementing network segmentation and access controls can help contain the spread of the botnet within the network. By dividing the network into smaller, isolated segments and restricting communication between them, organizations can prevent the lateral movement of botnet infections and limit their impact on critical systems and data.
- Monitor network traffic for signs of further botnet activity: Continuous monitoring of network traffic is essential for detecting signs of further botnet activity and preventing reinfection. Network security solutions like IDS and Security Information and Event Management (SIEM) systems can provide real-time visibility into network activity, allowing administrators to identify and respond to botnet-related threats promptly.
5.3 Tools and Techniques:
- Network security appliances like firewalls and intrusion prevention systems (IPS): Firewalls and IPS play a critical role in blocking malicious network traffic associated with botnet communication. These appliances can be configured to inspect incoming and outgoing traffic, block connections to known botnet C&C servers, and prevent unauthorized access to sensitive network resources.
- Endpoint security solutions with botnet detection capabilities: Endpoint security solutions equipped with botnet detection capabilities can help identify and remove botnet malware from infected devices. These solutions use advanced detection algorithms and behavioral analysis techniques to detect and mitigate botnet-related threats, protecting endpoints from compromise.
- Threat intelligence feeds to identify known botnet command-and-control servers: Threat intelligence feeds provide valuable information about known botnet C&C servers and malicious IP addresses. By subscribing to threat intelligence feeds and integrating them into security solutions, organizations can proactively block connections to known botnet infrastructure and reduce the risk of botnet infections.
6. Spyware
6.1 Objective:
Detect and remove spyware, mitigate data exposure risks, and educate users on safe online behavior.
6.2 Steps:
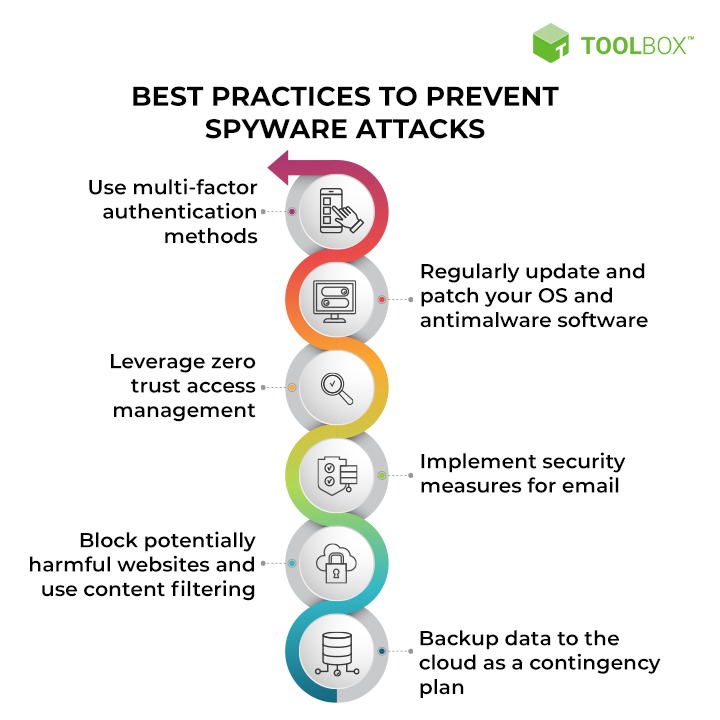
- Identify symptoms of spyware infection, such as browser redirects or pop-up ads: Recognizing common symptoms of spyware infection is the first step in detecting and mitigating its impact. Symptoms may include unexpected browser behavior such as frequent redirects to unfamiliar websites, the appearance of intrusive pop-up ads, or changes to browser settings without user consent.
- Scan systems with antivirus or antimalware software to detect and remove spyware: Conducting regular scans of systems with antivirus or antimalware software is essential for detecting and removing spyware infections. These tools utilize signature-based detection and heuristic analysis to identify malicious software, including spyware, and remove it from infected systems.
- Reset browser settings to default and remove unwanted extensions: Spyware often infiltrates systems through malicious browser extensions or changes to browser settings. Resetting browser settings to their default configurations and removing any unwanted or suspicious extensions can help eliminate spyware-related components and restore browser security and performance.
- Educate users about the risks of downloading suspicious software or clicking on unknown links: User education is critical for preventing spyware infections and promoting safe online behavior. Training programs should educate users about the risks associated with downloading software from untrusted sources, clicking on unknown links in emails or social media posts, and engaging in other risky online activities that may expose them to spyware threats.
- Implement web filtering and endpoint protection solutions to block spyware downloads: Implementing web filtering and endpoint protection solutions can help block access to malicious websites known for distributing spyware and other types of malware. Web filtering solutions can restrict access to websites based on predefined categories or URLs associated with known spyware distribution networks, while endpoint protection solutions can detect and block spyware downloads in real-time.
6.3 Tools and Techniques:
- Antispyware software like Spybot Search & Destroy or Malwarebytes:Dedicated antispyware software such as Spybot Search & Destroy or Malwarebytes can be used to scan and remove spyware infections from infected systems. These tools employ advanced detection algorithms and malware removal capabilities to identify and eliminate spyware-related threats, protecting users' privacy and sensitive information.
- Browser security extensions to block malicious websites: Browser security extensions like uBlock Origin or Bitdefender TrafficLight can help block access to malicious websites known for distributing spyware and other types of malware. These extensions use blacklist-based filtering and heuristic analysis to identify and block potentially harmful web content, providing an additional layer of protection against spyware threats.
- User training and awareness programs on recognizing and avoiding spyware threats: User training and awareness programs should educate users about the signs of spyware infection, such as unusual browser behavior or unexpected pop-up ads, and provide guidance on how to avoid spyware threats. Training materials may include information on safe browsing practices, the importance of keeping software up-to-date, and how to recognize and avoid common spyware distribution methods.
7. Adware
7.1 Objective:
Remove adware from infected systems, block unwanted advertisements, and enhance browser security.
7.2 Steps:
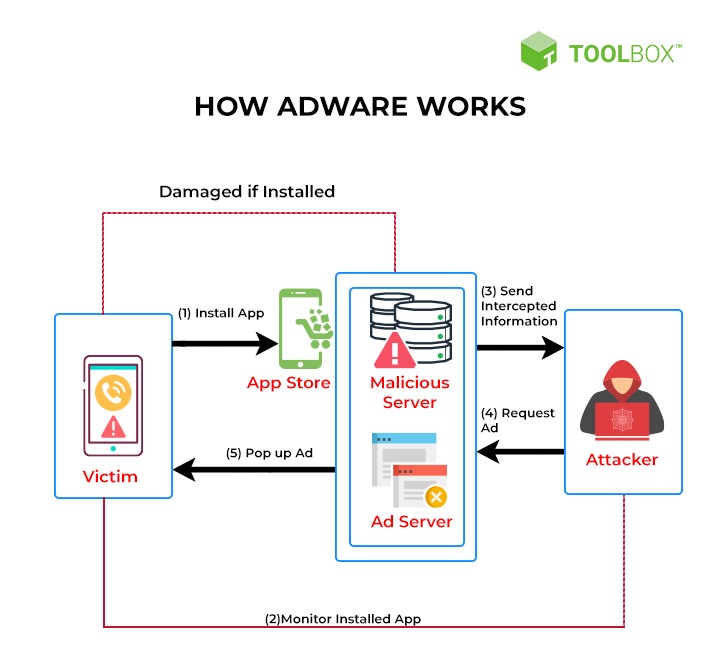
- Identify adware symptoms such as intrusive pop-up ads or browser redirects: Recognizing symptoms associated with adware infections is crucial for effectively removing adware from infected systems. Symptoms may include the sudden appearance of intrusive pop-up ads, browser redirects to unfamiliar websites, or changes to browser settings without user consent.
- Scan systems with adware removal tools to detect and remove adware: Conducting thorough scans of systems with dedicated adware removal tools is essential for detecting and removing adware infections. Tools like AdwCleaner or Bitdefender Adware Removal Tool use signature-based detection and heuristic analysis to identify and eliminate adware-related components from infected systems, restoring browser security and performance.
- Reset browser settings to remove unwanted extensions and restore default configurations: Adware often infiltrates systems through malicious browser extensions or changes to browser settings. Resetting browser settings to their default configurations and removing any unwanted or suspicious extensions can help eliminate adware-related components and restore browser security and functionality.
- Install ad blockers or browser security extensions to prevent adware from displaying ads: Installing ad blockers or browser security extensions can help prevent adware from displaying unwanted advertisements and further compromising system security. Ad blocking extensions like uBlock Origin or AdBlock Plus can effectively block intrusive ads and prevent adware from displaying advertisements while browsing the internet.
- Educate users on safe browsing habits and avoiding suspicious downloads: User education is essential for preventing adware infections and promoting safe browsing habits. Training programs should educate users about the risks associated with downloading software from untrusted sources, clicking on suspicious links or ads, and engaging in other risky online activities that may expose them to adware threats.
7.3 Tools and Techniques:
- Adware removal tools like AdwCleaner or Bitdefender Adware Removal Tool:Dedicated adware removal tools such as AdwCleaner or Bitdefender Adware Removal Tool can be used to scan and remove adware infections from infected systems. These tools employ advanced detection algorithms and malware removal capabilities to identify and eliminate adware-related components, restoring browser security and functionality.
- Ad blocking browser extensions such as uBlock Origin or AdBlock Plus:Ad blocking browser extensions like uBlock Origin or AdBlock Plus can effectively block intrusive ads and prevent adware from displaying advertisements while browsing the internet. These extensions use blacklist-based filtering and heuristic analysis to identify and block potentially harmful web content, providing users with an additional layer of protection against adware threats.
- Browser security settings to block pop-up ads and disable automatic downloads: Configuring browser security settings to block pop-up ads and disable automatic downloads can help prevent adware from compromising system security. Users should adjust browser settings to block pop-up windows, disable automatic downloads of files or software updates, and enable built-in security features like Safe Browsing to protect against adware threats while browsing the internet.
8. Phishing Attack
8.1 Objective:
Identify and mitigate phishing attempts, educate users on recognizing phishing emails, and implement email security measures to prevent future attacks.
8.2 Steps:
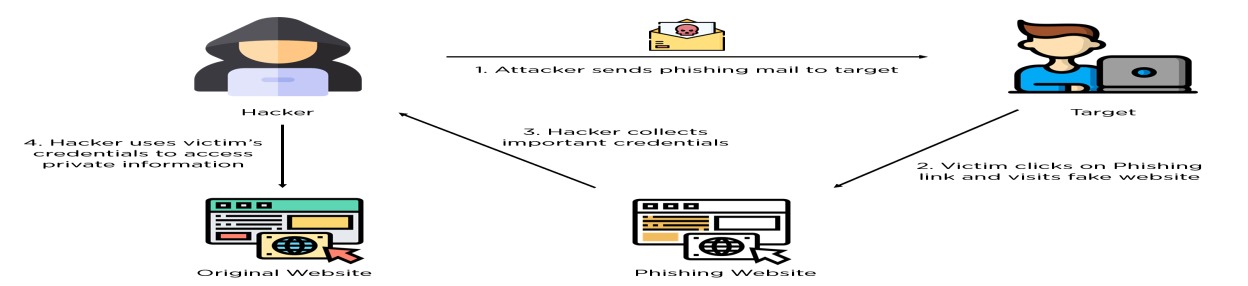
- Identify phishing emails by analyzing sender addresses, email content, and embedded links: Phishing emails often contain suspicious sender addresses, grammatical errors, urgent requests, or embedded links leading to malicious websites. Training users to recognize these indicators can help identify phishing attempts and avoid falling victim to them.
- Train users to recognize phishing attempts and report suspicious emails promptly: Educating users about the characteristics of phishing emails and providing training on how to recognize and report suspicious emails promptly is crucial for mitigating phishing attacks. Phishing simulation and training platforms like KnowBe4 or PhishMe can be used to simulate phishing attacks and train users on how to respond effectively.
- Implement email filtering and scanning to block phishing emails before they reach users' inboxes: Deploying email security solutions that include filtering and scanning capabilities can help block phishing emails before they reach users' inboxes. These solutions analyze email headers, content, and attachments to identify and block phishing attempts, reducing the risk of users inadvertently falling victim to them.
- Investigate reported phishing emails to determine if any users have fallen victim: Promptly investigating reported phishing emails is essential for determining if any users have fallen victim to phishing attempts. By analyzing email headers, sender addresses, and user interactions, administrators can identify compromised accounts and take appropriate remediation measures to prevent further damage.
- Enhance email authentication with techniques like SPF, DKIM, and DMARC to prevent email spoofing: Implementing email authentication protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) can help prevent email spoofing and protect against phishing attacks. These techniques verify the authenticity of email senders and prevent malicious actors from impersonating legitimate domains.
8.3 Tools and Techniques:
- Email security solutions like Proofpoint or Mimecast for email filtering and scanning: Email security solutions such as Proofpoint or Mimecast offer advanced filtering and scanning capabilities to detect and block phishing emails before they reach users' inboxes. These solutions analyze email headers, content, and attachments for signs of phishing attempts and provide administrators with tools to manage and mitigate email security risks.
- Phishing simulation and training platforms such as KnowBe4 or PhishMe:Phishing simulation and training platforms like KnowBe4 or PhishMe allow organizations to simulate phishing attacks and train users on how to recognize and respond to phishing attempts effectively. These platforms provide customizable phishing templates, interactive training modules, and reporting tools to help organizations strengthen their security awareness and resilience against phishing attacks.
- Email authentication protocols (SPF, DKIM, DMARC) to prevent email spoofing: Implementing email authentication protocols such as SPF, DKIM, and DMARC can help prevent email spoofing and protect against phishing attacks. SPF verifies that the sending mail server is authorized to send email on behalf of a domain, DKIM adds a digital signature to email messages to verify their authenticity, and DMARC provides policies for handling emails that fail authentication checks, reducing the risk of phishing attacks targeting domain impersonation.
9. Distributed Denial of Service (DDoS) Attacks
9.1 Objective:
Mitigate the impact of DDoS attacks, maintain service availability, and implement proactive measures to prevent future attacks.
9.2 Steps:
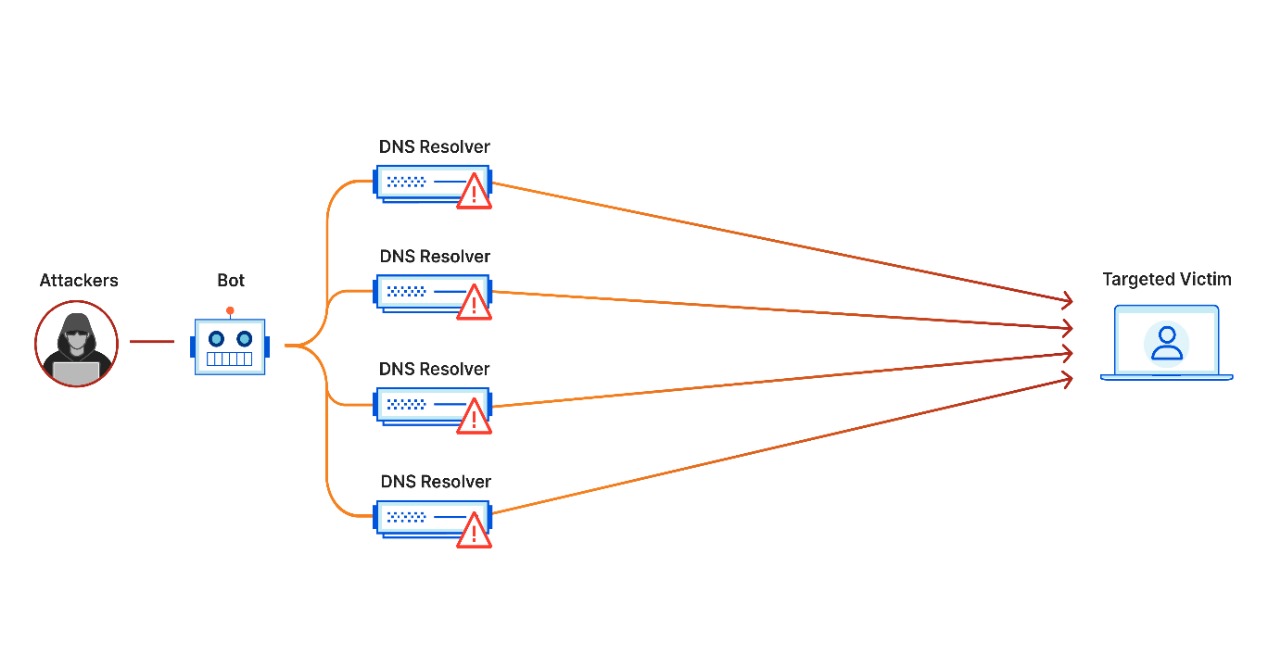
- Identify the source and type of DDoS attack (e.g., volumetric, protocol-based, application layer): Understanding the type and source of a DDoS attack is crucial for effectively mitigating its impact. Volumetric attacks flood network bandwidth, while protocol-based attacks target network infrastructure, and application layer attacks exploit vulnerabilities in web applications. Identifying the specific characteristics of the attack enables responders to deploy appropriate countermeasures.
- Redirect traffic through DDoS mitigation services or scrubbing centers to filter out malicious traffic: DDoS mitigation services and scrubbing centers provide dedicated infrastructure for filtering out malicious traffic and mitigating the impact of DDoS attacks. By redirecting traffic through these services, organizations can identify and block DDoS attack traffic while allowing legitimate traffic to reach its intended destination, thereby maintaining service availability.
- Implement rate limiting and access controls to mitigate the impact of DDoS attacks on critical resources: Rate limiting and access controls can help mitigate the impact of DDoS attacks on critical resources by limiting the amount of traffic allowed to access these resources. By imposing rate limits on incoming requests and implementing access controls to restrict access to vulnerable services, organizations can minimize the impact of DDoS attacks and ensure the availability of essential services.
- Monitor network traffic and server performance to detect and respond to DDoS attacks in real-time: Real-time monitoring of network traffic and server performance is essential for detecting and responding to DDoS attacks promptly. Intrusion detection and prevention systems (IDPS) can analyze network traffic patterns and identify signs of a DDoS attack, triggering automated response mechanisms to mitigate the impact on affected systems.
- Collaborate with internet service providers (ISPs) and DDoS mitigation vendors to mitigate large-scale attacks: Collaboration with ISPs and DDoS mitigation vendors is critical for mitigating large-scale DDoS attacks that exceed the organization's capacity to handle independently. ISPs can implement traffic filtering upstream to block DDoS attack traffic before it reaches the organization's network, while DDoS mitigation vendors can provide additional resources and expertise to mitigate the attack effectively.
9.3 Tools and Techniques:
- DDoS mitigation services and appliances like Cloudflare or Akamai:DDoS mitigation services and appliances such as Cloudflare or Akamai offer dedicated infrastructure and services for mitigating the impact of DDoS attacks. These services leverage advanced traffic filtering and mitigation techniques to identify and block malicious traffic, ensuring the availability of critical services during DDoS attacks.
- Intrusion detection and prevention systems (IDPS) to detect and block DDoS attack traffic: Intrusion detection and prevention systems (IDPS) can detect and block DDoS attack traffic by analyzing network traffic patterns and identifying signs of malicious activity. These systems can automatically trigger response mechanisms to mitigate the impact of DDoS attacks on affected systems, helping maintain service availability.
- Traffic analysis tools like Arbor Networks or Radware to monitor network traffic patterns: Traffic analysis tools like Arbor Networks or Radware provide real-time visibility into network traffic patterns, allowing organizations to monitor for signs of a DDoS attack. By analyzing network traffic in real-time, organizations can detect and respond to DDoS attacks promptly, minimizing disruption to business operations.
10. Conclusion:
In the journey towards enhancing cybersecurity resilience, the Data Theft Playbook stands as a steadfast ally, empowering Red Teams to conduct exhaustive assessments of an organization's security defenses and incident response capabilities. Through the meticulous simulation of real-world data theft scenarios, Red Teams illuminate vulnerabilities, expose gaps in defenses, and identify procedural weaknesses, enabling organizations to proactively fortify their security posture. By embracing a culture of continuous testing, collaboration, and improvement, organizations can navigate the ever-evolving threat landscape with confidence, effectively mitigating the risk of data breaches and unauthorized access, thus safeguarding sensitive information and upholding trust with stakeholders.