User Awareness Training - Gap Analysis
Redback Operations Cybersecurity User Awareness Training
Document Creation: 27 Jul, 2024. Last Edited: 03 Aug, 2024. Authors: Tristan Apperley.
Effective Date: 03 Aug 2024. Expiry Date: 03 Aug 2025.
Purpose
The Purpose of this gap analysis is to identify the current level of cyber security awareness knowledge across Redback Operations and compare it to industry recommendations.
This document includes a company-wide survey and the results which are then used to make recommendations on what should be included in Redback Operations annual awareness training packages.
Survey Results
The following survey was conducted via a Survey Monkey survey between the 27 Jul and 03 Aug 24 and can be viewed here - Awareness Training Survey
The following questions, answers and results were included in the survey:
1. How often should you update your software and Antivirus?
- Once a week
- Once a Month
- When we are told to
- Never
Q1 Responses:
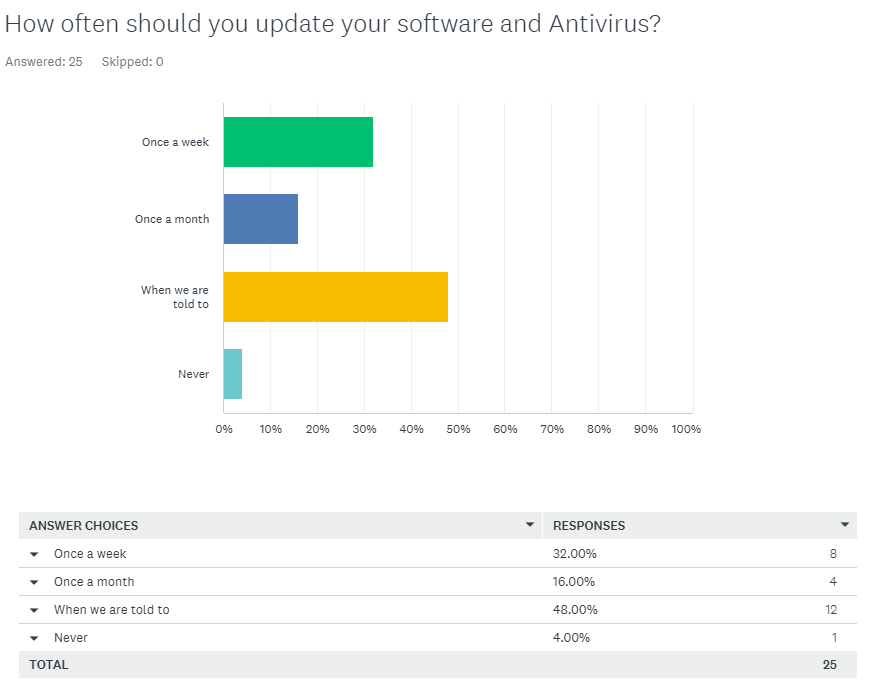
Q1 Comment/Assesment:
Overall, most members of Redback Operations regularly update their software and antivirus. Training to emphasise the importance of this practice may help ensure that all company members keep their systems current and address security issues promptly.
2. Are you aware of Two Factor Authentication and do you use it?
- Yes - I use it
- Yes - But i don't use it
- No I don't know what it is
Q2 Responses:
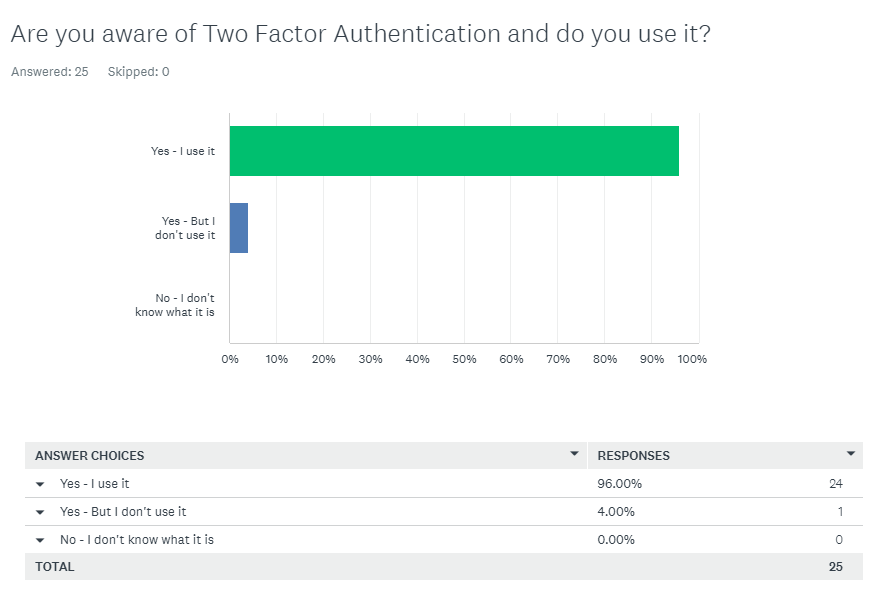
Q2 Comment/Assesment:
All members of Redback Operations are familiar with Two-Factor Authentication, with all but one member using it. This topic will not need extensive coverage in the Security Awareness Training package.
3. What type of password do you use?
- Default/Basic
- Complex
- Passphrases
- I use a password manager
Q3 Responses:
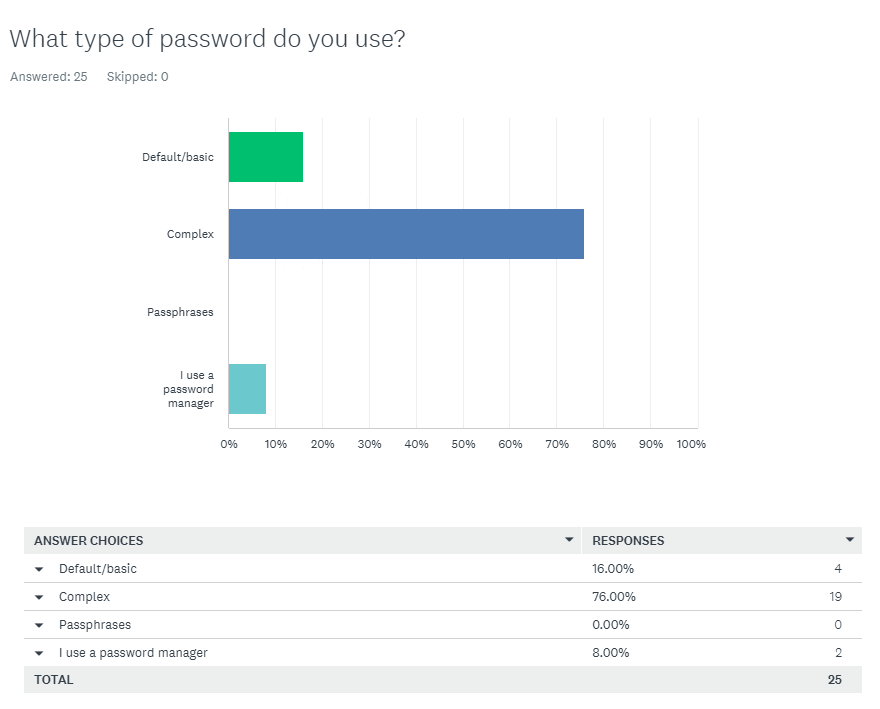
Q3 Comment/Assesment:
While most members of Redback Operations use complex passwords or a password manager, it is concerning that 16% of respondents reported using basic or default passwords. Training should address why this is a significant security risk and emphasise the importance of using secure passwords.
4. Do you store your password anywhere (physically or online) and do you share you password with anyone (please select all that apply)?
- Yes - I store my password somewhere
- No my password is not stored anywhere
- I do share my password with other people
Q4 Responses:
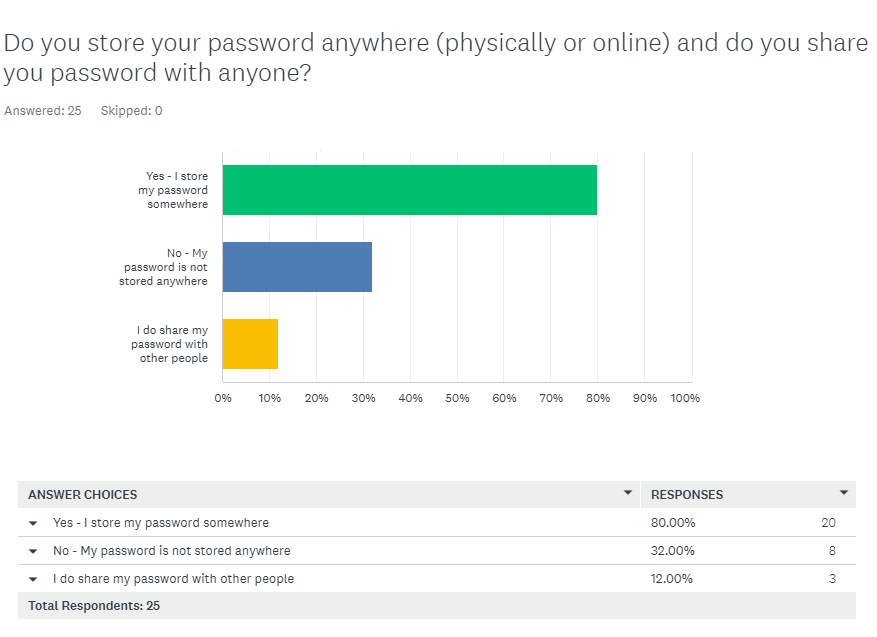
Q4 Comment/Assesment:
It is concerning that 80% of respondents indicated they store passwords (physically or online), and even more concerning that 12% share passwords with others. This issue will need to be addressed in the Security Awareness Training.
5. Do you understand what is meant by Clear Desk Policy and do you lock your device when you leave it unattended (please select all that apply)?
- Yes - I am aware of what a Clear Desk Policy is
- No - I am not aware of what a Clear Desk Policy is
- Yes - I do lock my device when I leave it
- No - I do not lock my device when I leave it
Q5 Responses:
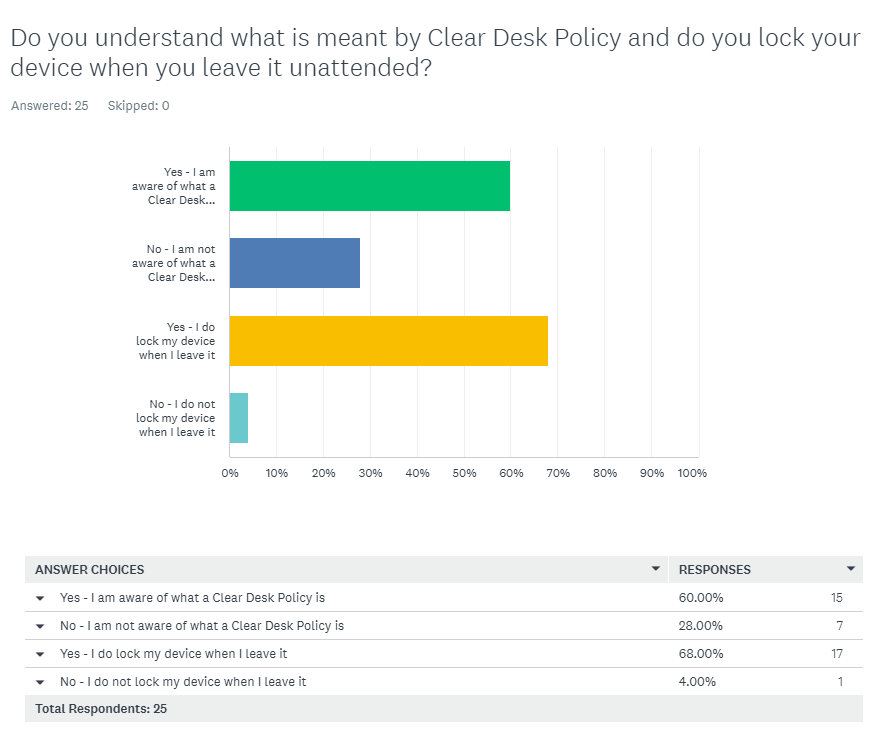
Q5 Comment/Assesment:
Approximately one-third of the company is unaware of the Clean Desk Policy requirement, so this topic will be reviewed in the Security Awareness Training. While all but one member locks their terminals when away, this good practice does not require detailed coverage in the training.
6. What do you do when you receive an email with a link or document embedded?
- I would verify it’s from a source I trust, before clicking on the link
- I would click on the link without hesitation
Q6 Responses:
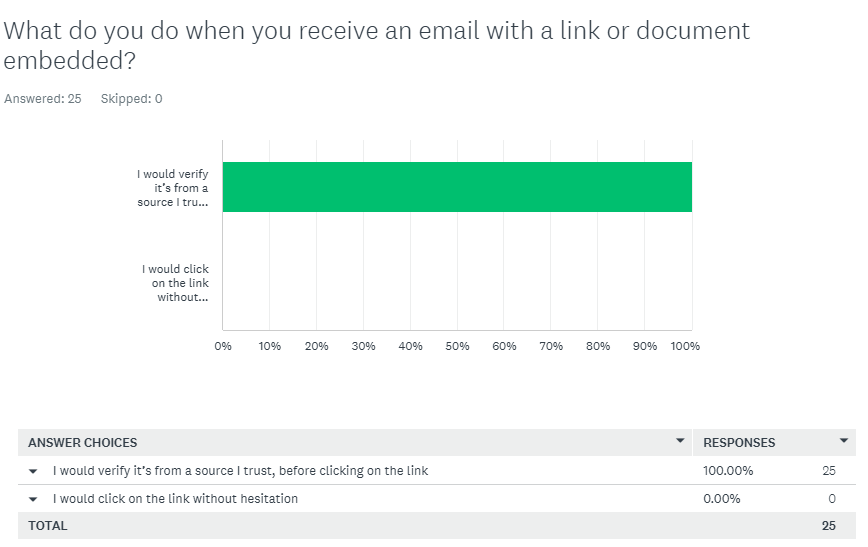
Q6 CComment/Assesment:
All respondents seem to understand what to do if they receive a link or document from an unknown source. Despite this good result, the significant risk posed by such attacks warrants thorough coverage in the Security Awareness Training.
7. What would you do if you identified a security issue or breach?
- I would inform the company IT help desk
- I would fix it myself
- I would ignore it
Q7 Responses:
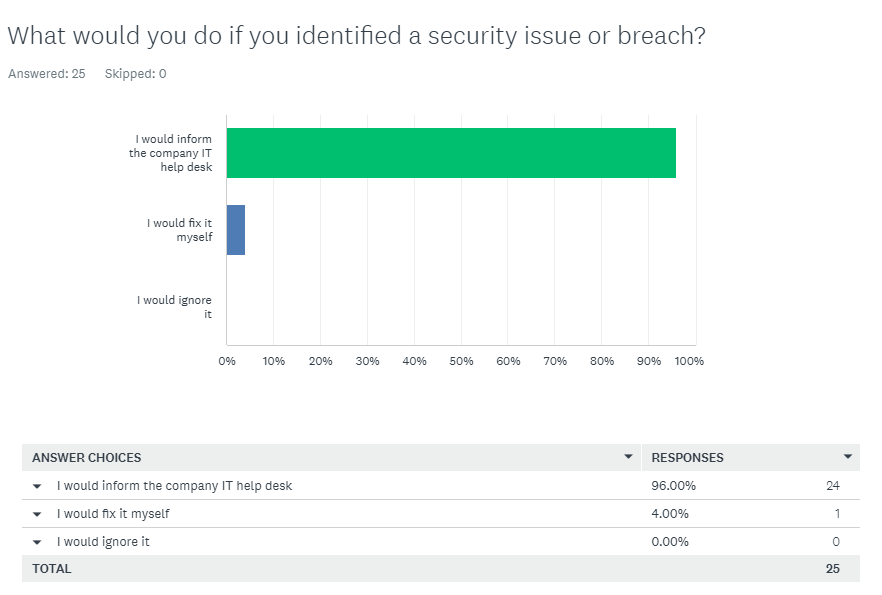
Q7 Comment/Assesment:
It is very encouraging that all but one member would report a security issue or breach to the IT help desk as soon as they are aware of it. Therefore, the focus of this topic in the Security Awareness Training package should be on who to contact rather than why.
8. When did you last conduct Security awareness training for Redback Operations?
- In the last 6 months
- in the last 6-12 months
- Greater then 12 months
- Never
Q8 Responses:
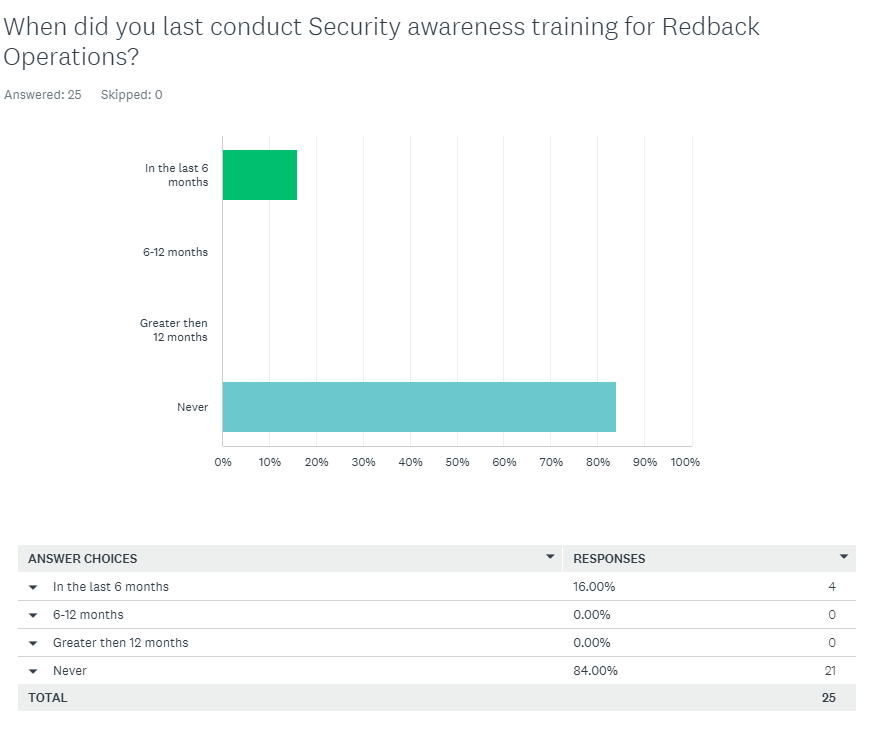
Q8 Comment/Assesment:
Over 80% of Redback Operations staff have not participated in a Security Awareness Training package for the company, highlighting the need for this package to be developed.
9. Please select all that apply
- I use company devices on public Wi-Fi i.e. at the Airport, Shops etc
- I back up my files in accordance with Redback Operations requirements
- I use Redback Operations devices for private use?
- I use a VPN when required
- I use encryption when storing and sending personal data
- I keep up to date with current Cyber Security Threats and the best way to defend and mitigate them?
- I am aware of Redback Operation’s procedures when it comes to disposing of old devices that contain sensitive information
Q9 Responses:
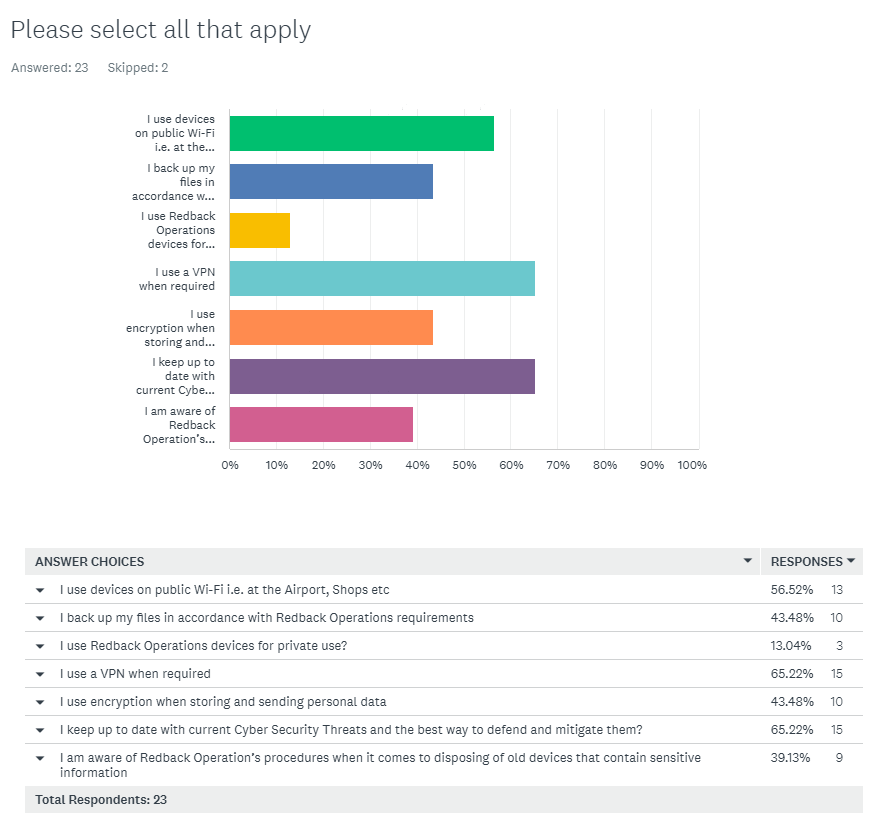
Q9 Comment/Assesment:
To better understand the daily operations of Redback Operations staff, the following points were noted:
- Public Wi-Fi: Over half of the company uses public Wi-Fi. Ensuring users are aware of steps to take to stay safe while using public Wi-Fi should be included in the Security Awareness Training.
- Backups: Less than half of the company backs up their files according to Redback Operations Policy. This issue needs to be addressed in the Security Awareness Training package.
- VPN: Two-thirds of the company use a VPN as required, which is a good result. However, the need for and benefits of VPNs should be emphasised in the Security Awareness Training to increase usage.
- Encryption: Less than half of the staff use (or are aware they use) encryption for storing and sending data. How and why to do this should be covered in the Security Awareness Training package.
- Current Threats: Approximately two-thirds of the company stay informed about current IT threats. While this area doesn’t need to be included in the Security Awareness Training package, a method for keeping the company updated on current news should be explored further.
- Disposal of Hardware Storage Devices: Although Redback Operations has limited storage devices, everyone must be aware of how to store and dispose of sensitive data appropriately, which should be covered in the Security Awareness Training.
Overall Comments:
As expected for a tech company, the overall cybersecurity knowledge across the company is quite good. While some areas need attention, the most significant issue is the lack of formalised annual or onboarding training packages.
Recommendation:
Given the solid baseline knowledge of all employees, it is recommended to create a Security Awareness Training package covering the Australian Signal Directorate (ASD)/Australian Cyber Security Centre (ACSC) "6 Practical Ways to Protect Yourself Online." The six topics are:
- Update your device
- Set up and perform regular backups
- Turn on multi-factor authentication
- Set secure passphrases
- Recognise and report scams
- Watch out for threats
These topics should form six modules, with each ASD/ACSC topic providing the core content for a module. Additional, more specific content (likely from other ACSC webpages) will also need to be included in each module to ensure the Security Awareness Training is current and applicable to Redback Operations.